Image
Software Algorithm and Hardware Implementations of Information Security Using Number Theory and Chaotic Systems
Research Project
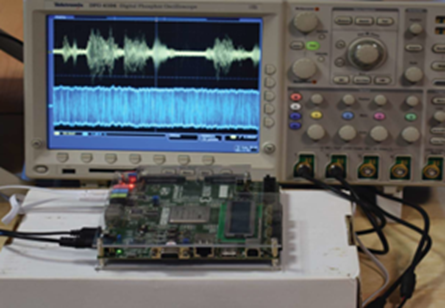
The project aims at proposing novel software algorithms for information security and their hardware implementations. The algorithms will utilize different methods based on number theory and chaos theory. Cryptography and information hiding systems will be developed for different media data types such as text, image, audio and video. The project will investigate different classes of symmetric/asymmetric and stream/block ciphers. In addition, it will explore both steganography and watermarking in spatial and frequency domains. The proposed information security solutions will be evaluated using standard performance measures. The project targets achieving technical outcomes that include hardware prototypes and a website.
Objective/Contributions:
- Use chaos theory to design new information security techniques that extend on the previously developed research in different directions.
- Use number theory in the design of new information security techniques.
- Develop a hardware prototype that includes realizations of some of the information security techniques designed in objectives 1 and 2.
- Develop a website that includes implementations of the designed information security techniques.
- Publications, Master degrees, conferences and community services.